We have spent a couple of weeks seeing how a couple of accounts from different content creators are going down, YouTube, Twitch, Facebook, are just some of the networks that have presented some problems, but is it a direct security failure of social networks? ? In this post we will explain how these almost massive attacks are being carried out.
Ever since the Internet existed, it has been a door for downloading different types of programs, from paid software to free software, and as always, you cannot miss a program that has been modified to be used by removing the restrictions and releasing it to the public. , this is known as “crack”. A crack allows you to get rid of the limitations, thus allowing you to avoid paying for a program, but this is not a good practice at all, since it is well known that security problems love this practice. The Trojan Horse is a clear example of how these released software works, they offer you something for free, which you should pay for a license, and in exchange, they install malware on your computer.
And here an interesting question arises, how come antiviruses do not detect these malicious programs? Antiviruses have the mission of defending us from different types of attacks, but these are increasingly being created with more ingenuity, operating silently, trying to avoid being detected, but if a user downloads a crack, it will not allow him to be installed on the computer until deactivating the antivirus, and this is the first step to suffer a large-scale attack.
Let's take the following case, you want to look for a crack of a program, and you find the following results:
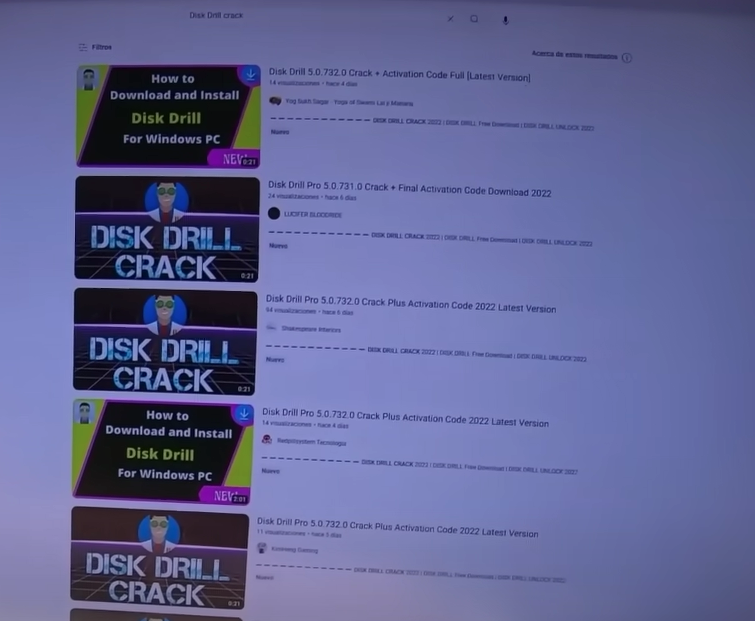
With this, you can already see that there are many links offering the solution to your problem, we download the program or crack in question, but when you want to install, it is likely that the antivirus launches an alert.
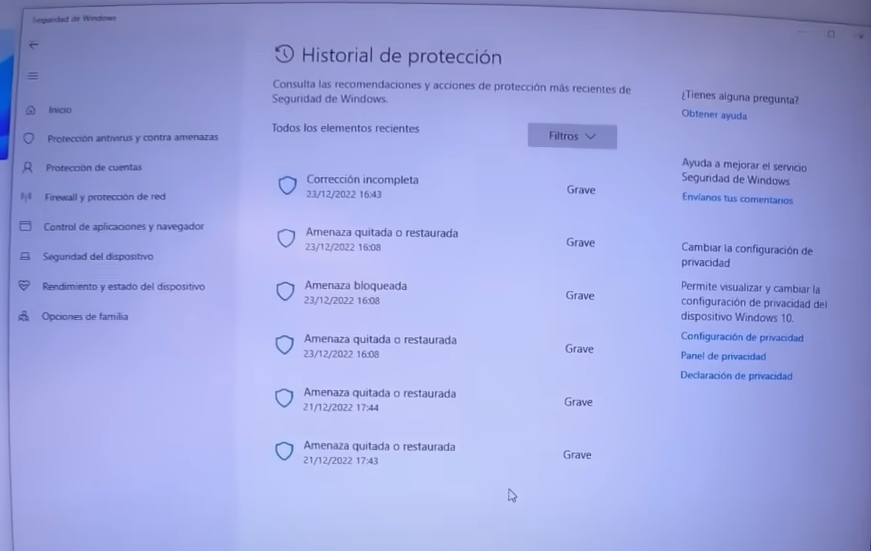
So, it is when the war has already happened, if there are saved passwords in your browser, it is likely that they are already in the hands of cybercriminals.
Here we explain the way the attackers use:
This is a database of different people who have been hacked, using the stolen cookie files, when the infection occurs, the files that the cybercriminals seek to obtain on your computers are the cookies, the same ones that the browser asks you from time to time if you want to accept, and the ones that some cleaners like ccleaner kindly offer to delete.
Once they are stolen, they go through a cookie checker, in order to identify which service or application they correspond to, thus generating a large number of cookies from different services.
The filters allow you to know a lot of information about the accounts, such as, for example, the number of subscribers or followers, the number of videos uploaded, or if there is any associated payment method, to use them is done as follows:
For a Twich account, for example, they open the web, and with a cookie manager, the cookies obtained from the victim are imported.
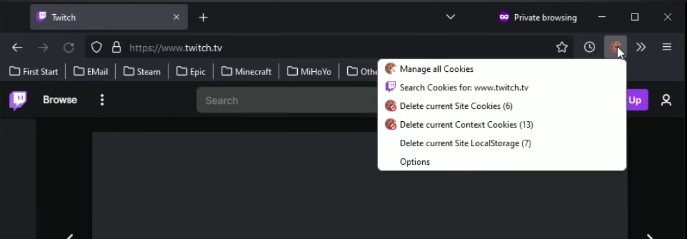
These managers can be downloaded from the internet without any restrictions, and they have different types of uses, we must make it clear that they are tools, but they are misused in the end.
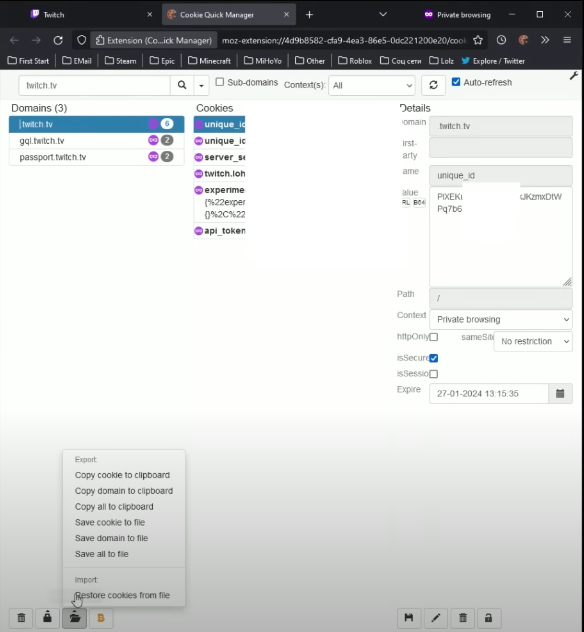
Once the cookie is imported, a window is displayed informing that you are ready, the page is refreshed and that's it.
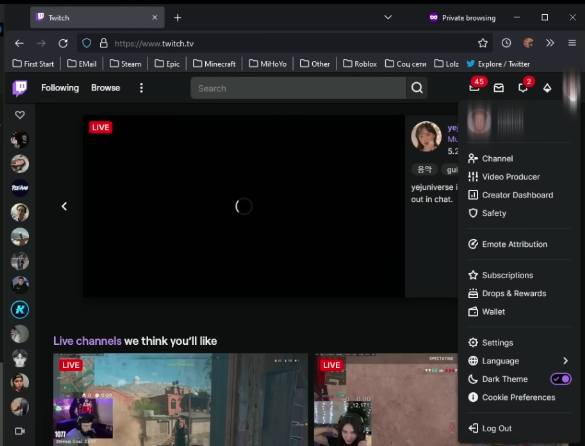
You are already inside the channel of the person who was the victim at some point, having access to everything you need, in addition, complementing this theft with stealing browser passwords, in some cases there is not much to do.
This has happened to many content creators, as we indicated at the beginning, even creators of cybersecurity issues have been affected, to avoid it, we leave you with a list of recommendations to follow and not fall into these traps .
- Never download pirated programs
- Do not disable your antivirus to install any program
- If you have doubts about a software or link, you can pass it through online scanners such as virustotal.com
- Delete your browser cookies frequently, either manually or with a program
- Try as much as possible to never save passwords in your browser.

